Introduction
The Metasploit Framework (MSF) is far more than just a collection of exploits. It’s an infrastructure that you can build upon and utilize for your custom needs. This allows you to concentrate on your unique environment, and not have to reinvent the wheel. I consider the MSF to be one of the single most useful auditing tools freely available to security professionals today. From a wide array of commercial grade exploits and an extensive exploit development environment, all the way to network information gathering tools and web vulnerability plugins, the Metasploit Framework provides a truly impressive work environment.
This course has been written in a manner to encompass not just the front end “user” aspects of the framework, but rather give you an introduction to the capabilities that Metasploit provides. We aim to give you an in depth look into the many features of the MSF, and provide you with the skill and confidence to utilize this amazing tool to its utmost capabilities.
Updates
Normally to update Metasploit, you simply run “mfsupdate”, but according to the Rapid 7 website,Metasploit updates are synced to update weekly with Kali.
(https://community.rapid7.com/thread/3007)
Metasploit Overview
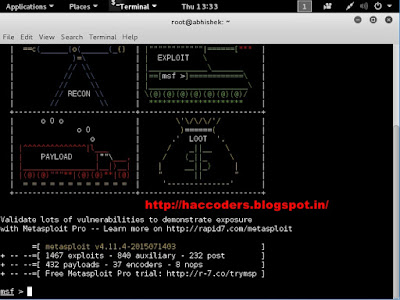
You can start Metasploit Simple Type On Terminal "msfconsole"Once Metasploit loads you will see the following main screen and be given an “msf >” prompt.
Metasploit can be a little confusing if you have never used it before, but once you get used to how it works, you can do some amazing things with it.
Basically, using Metasploit to attack a target system usually involves:
1. Picking an Exploit
2. Setting Exploit Options
3. Picking a Payload
4. Setting Payload Options
5. Running the Exploit
6. Connecting to the Remote System
7. Performing Post Exploitation Processes
The screenshot below shows an example of this process, but don’t worry; we will cover the process in much more detail as we go along.
Depending on the type of exploit, once our exploit is complete we will normally end up with either a remote shell to the computer or a Meterpreter shell.
A remote shell is basically a remote terminal connection or a text version of a remote desktop for Windows users. It allows us to enter commands as if we are sitting at the keyboard.
But a Meterpreter shell offers a ton of interesting programs and utilities that we can run to gather information about the target machine, control devices like the webcam and microphone, or even use this foothold to get further access into the network.
And of course, if needed, you can drop to a regular shell at any time.
In most cases, depending on what you are trying to do, a Meterpreter Shell is much more advantageous than just a regular shell.
We will discuss the Meterpreter Shell later, but for now let’s quickly cover the first five steps.
Tech Note:
When all else fails and you start to feel lost in
Metasploit, or the Meterpreter shell, try typing
the “help” command.
You can also use the “tab” key to autocomplete a
line or hit it twice to show all available exploits
and payloads.
Ex. show exploits <tab><tab>
Picking an Exploit
If you are a glutton for punishment and want to view all the exploits, just type “show exploits” from the msf prompt:
msf > show exploits
But
it is easier to use the search command to find what you are looking
for. Simply type “search” and then the information you want. Sometimes
being very specific will help you find the exploit you want quicker.
Tech Note:
If you see an error that says, “[!] Database not
connected or cache not built, using slow
search” all you need to do is start the PostSQL
Database before running msfconsole (though
your search will work without it running, it will
just be slower).
To start the Database at a terminal prompt, type
the following:
● service postgresql start
● service metasploit start
● msfconsole
Metasploit
allows you to search for exploits in multiple ways, by platform, or
even CVE (Common Vulnerabilities and Exposures) and bugtrack numbers.
Type “help search” to see all of the options:
To see a specific CVE ID number:
To see all the CVE ID’s from this year (truncated list):
Or to see exploit information for a particular program just use its name:
msf > search unreal
When you see an exploit that you want to know more about, just copy and paste the full path name and use the info command:
msf > info exploit/unix/irc/unreal_ircd_3281_backdoor
This will display the full information screen for the exploit:
The information screen shows the author’s name, a brief overview (not shown) along with the basic options that can be set, a description and website security bulletin references for the exploit (shown).
As you can see in the picture above, we can set a couple options for this exploit, which leads us into our next section.
But before we set our exploit options, we need to “use” it. Once we know we have the exploit we want, we simply run the “use” command with the exploit name. Again copying and pasting the exploit
path and name works very well here too:
Okay, we are now using our exploit, so how do we set the options?
Setting Exploit Options
Setting options in Metasploit is as simple as using the “set” command followed by the variable name to set and then the value.
set <Variable Name> <Value>
Tech Note:
LHOST = Local Host, or our
Kali System
RHOST = Remote Host, or
our target System
LPORT = Port we want to
use on our Kali System
RPORT = Port we want to
attack on our target System
To set what variables can be set, use the “show options” command:
This exploit only uses two main variables, RHOST and RPORT. Rhost is the remote host that we are attacking and Rport is the remote port.
Let’s go ahead and set the RHOST variable using the set command. If the target system’s IP address was 192.168.0.20 then we would use the set command below:
If we run the “show options” command again, we can see that the variable has indeed been set:
This is all you really need is set in this exploit. You could now run the “exploit” command to execute it.
If you are feeling a bit lost, don’t panic, we will cover this in more detail in the Metasploitable chapter.
Multiple Target Types
The Unreal backdoor was a fairly easy exploit to use. Some exploits have multiple variables that you need to set and they might even have some optional variables that can also be configured.
As you use Metasploit, you will find that some have multiple target types that can be attacked, and that the exact target needs to be set for the exploit to work properly. To see the target, enter “show targets”.
On the exploit we used above, the target is automatic, so we don’t need to set it.
But on others, there are numerous targets and we need to pick the right one.
Getting a remote shell on a Windows XP Machine
We took a brief look at one of the Linux exploits, let’s go ahead and run through the ms08-067 exploit
as it is one of the more popular Windows exploits.
1. To start, simply use the exploit:
msf > use exploit/windows/smb/ms08_067_netapi
2. Now type, “show options”:
Notice that by default the target is set to “Automatic Targeting”. I have had mixed results with using automatic targeting, and sometimes things work better if you set the exact target.
3. If we want to set a specific target type, “show targets”:
4. Then type, “set target <ID#>” to set the actual target
5. And again a “show options” will reveal that we indeed have the target value set:
Lastly, though not often used in regular exploits, we can also set advanced options if we want.
To show the advanced options, just type “show advanced”:
Now we have seen how to select an exploit and how to set the options. On many exploits we also
need to set a payload.
Picking a Payload
Metasploit comes with a multitude of different payloads that you can use. To see them, just type
“show payloads”:
Or you can type “set payload” and hit the tab key twice. This will prompt Metasploit to ask you if you
want to see all the available payloads:
Most of the payloads are laid out in the format of ‘Operating System/Shell Type’ as shown below:
● set payload/osx/x86/shell_reverse_tcp
● set payload/linux/x64/shell_reverse_tcp
● set payload/windows/shell_reverse_tcp
● set payload/windows/meterpreter/reverse_tcp
Simply select the correct OS for your target and then pick the payload you want.
The most popular types of payloads are shells, either a regular remote shell or a Meterpreter shell.
If we just want a remote terminal shell to remotely run commands, use the standard shell. If you want the capability to manipulate the session and run extended commands then you will want the Meterpreter shell (which we will discuss in further detail in the next chapter).
There are different types of ways that the payloads communicate back to the attacking system. I usually prefer reverse_tcp shells as once they are executed on the target system, they tell the attacking machine to connect back out to our Kali system.
The big advantage to this is that with the victim machine technically “initiating” the connection out, it usually is not blocked by the Firewall, as a connection trying to come in from the outside most likely will.
Once we know what payload we want to use, we set it using the “set” command.
6. So for our example let’s use a Meterpreter shell for a Windows system and have it connect
back to us via TCP:
Now that our payload is set, we just need to set the options for it.
Setting Payload Options
Payloads have options that are set in the exact same way that the exploit is set. Usually payload settings include the IP address and port for the exploit to connect out to.
And these too are set with the “set” command.
7. Type “show options” to see what settings the payload needs:
As you can see in the image above, a new section titled “Payload options” shows up when we run the command. We also have three new options that we can set, “EXITFUNC, LHOST, and LPORT”.
We will leave the EXITFUNC and LPORT settings to the default.
8. But we need to put in the LHOST or local host address. This is the IP address for our Kali system:
Once our payload options are set, we can go ahead and run the exploit.
Running the Exploit
When starting out, it is always a good idea to run the “show options” command one last time and double check that everything is set correctly.
If you notice above, looks like we forgot to set the target system (RHOST) IP address!
We set the RHOST for a prior example, but when we switched exploits, we never re-set the remote
host IP address. This can happen when you are running through a lot of exploits, or attacking different
systems, so it is a good idea to double check your settings.
9. Set the RHOST option by typing:
set RHOST 192.168.0.20
Checking the options one last time, everything looks good:
Our payload is selected, and all the options that we need to set are set.
We can now run the exploit.
10. To do so, simply use the “exploit” command.
The exploit then runs and when successful the payload executes and if the exploit works, we get a
remote connection.
Connecting to a Remote Session
Once we have a successful exploit we will be able to view any remote sessions that were created. To
check what sessions were created type the “sessions” command.
Any sessions that were created will show up along with the IP address, computer name and user name
of the target system.
We can now connect to the session interactively with the “sessions -i <ID#>” command as shown in the sample session above.
When we connect to the session, the prompt will change into a meterpreter prompt:
We will cover the Meterpreter shell in more depth in the next chapter. But for now, if we just type the “shell” command we can see that we do indeed have a remote shell to the Windows system.






































I was searching for loan to sort out my bills& debts, then i saw comments about Blank ATM Credit Card that can be hacked to withdraw money from any ATM machines around you . I doubted thus but decided to give it a try by contacting {skylinktechnes@yahoo.com} they responded with their guidelines on how the card works. I was assured that the card can withdraw $5,000 instant per day & was credited with $50,000 so i requested for one & paid the delivery fee to obtain the card, i was shock to see the UPS agent in my resident with a parcel{card} i signed and went back inside and confirmed the card work's after the agent left. This is no doubts because i have the card & has made used of the card. This hackers are USA based hackers set out to help people with financial freedom!! Contact these email if you wants to get rich with this Via email skylinktechnes@yahoo.com or whatsapp: +1(213)785-1553
ReplyDeleteHaven't you heard about cyber hacking company blank ATM card and how other people had benefited from it? I am Williams vivian by name, i want to share a blog and forums on how to get real blank ATM card,thank to cyber hacking company who helped me with an already hacked ATM CARD and i was so poor without funds that i got frustrated. One morning as i was browsing on the internet, i saw different comments of people testifying of how cyber hacking company helped him from being poor to a rich man through this already hacked ATM CARD. I was skeptical if this was true, i decided to contact him to know if he is real he proved to me beyond all doubts that its was really for real so i urgently receive my blank ATM card. Contact his email cyberhackingcompany@gmail.com and today am also testifying on how cyber hacking company helped me. I never believed in it until the card was sent to me, which am using today Contact the company now and become rich. Email: cyberhackingcompany@gmail.com
DeleteI was searching for job online about a month ago..It has really changed my life for good and now I can say I’m rich and I can never be poor again. The least money I get in a day with it is $10000.Only serious individuals should contact him because he is very straight forward and his series is 100% trusted i am a living testimony. Every now and then I keeping pumping money into my account and yes i am talking about the blank atm cards yes they are real. Though is illegal we all know, but there are no risks of being caught, because it has been programmed in such a way that it is not traceable,it also has a technique that makes it impossible for the CCTVs to detect you.. For details on how to get yours today, email the hackers on: bensadeghipourhackerones8@gmail.com
DeleteI was searching for job online about a month ago..It has really changed my life for good and now I can say I’m rich and I can never be poor again. The least money I get in a day with it is $10000.Only serious individuals should contact him because he is very straight forward and his series is 100% trusted i am a living testimony. Every now and then I keeping pumping money into my account and yes i am talking about the blank atm cards yes they are real. Though is illegal we all know, but there are no risks of being caught, because it has been programmed in such a way that it is not traceable,it also has a technique that makes it impossible for the CCTVs to detect you.. For details on how to get yours today, email the hackers on: bensadeghipourhackerones8@gmail.com
DeleteProviding T00LS & Tut0rials
DeleteSpam-ming
Hac-king
Car-ding
Scri-pting
Attac-king/Phishing
Kali-Linux
De-ep W-eb Course
With Complete guidence & Proper tools
Here I'm
@killhacks Telegram
7.5.2.8.2.2.0.4.0 I'C'Q
Fullz for Filling Benefits/SBA/Unemployment/Tax Returns
SSN DOB
SSN DOB DL
High Credit Fullz
CC FULLZ With CVV [vbv & non-vbv]
Minimum CS 700+
All valid & fresh Info
Invalid/wrong info will be replace
Fresh Spa-mmed
Contact
Tele'gram @leadsupplier
I'C'Q -> 7.5.2.8.2.2.0.4.0
I was searching for loan to sort out my bills& debts, then i saw comments about Blank ATM Credit Card that can be hacked to withdraw money from any ATM machines around you . I doubted thus but decided to give it a try by contacting {skylinktechnes@yahoo.com} they responded with their guidelines on how the card works. I was assured that the card can withdraw $5,000 instant per day & was credited with $50,000 so i requested for one & paid the delivery fee to obtain the card, i was shock to see the UPS agent in my resident with a parcel{card} i signed and went back inside and confirmed the card work's after the agent left. This is no doubts because i have the card & has made used of the card. This hackers are USA based hackers set out to help people with financial freedom!! Contact these email if you wants to get rich with this Via email skylinktechnes@yahoo.com or whatsapp: +1(213)785-1553
ReplyDelete
ReplyDeleteBE SMART AND BECOME RICH IN LESS THAN 3DAYS (williamshackers@hotmail.com)… It all depends on how fast you can be to get the new PROGRAMMED blank ATM card that is capable of hacking into any ATM machine,anywhere in the world. I got to know about this BLANK ATM CARD when I was searching for job online about a month ago..It has really changed my life for good and now I can say I'm rich and I can never be poor again. The least money I get in a day with it is about $50,000.(fifty thousand USD) Every now and then I keeping pumping money into my account. Though is illegal,there is no risk of being caught ,because it has been programmed in such a way that it is not traceable,it also has a technique that makes it impossible for the CCTVs to detect you..For details on how to get yours today, email the hackers on : (williamshackers@hotmail.com). Tell your loved once too, and start to live large. That's the simple testimony of how my life changed for good…Love you all …the email address again is email (williamshackers@hotmail.com)…
We will be getting a reverse TCP connection from the victim machine by using a small backdoor hack windows 7 using metasploit.
ReplyDeleteI was searching for job online about a month ago..It has really changed my life for good and now I can say I’m rich and I can never be poor again. The least money I get in a day with it is $10000.Only serious individuals should contact him because he is very straight forward and his series is 100% trusted i am a living testimony. Every now and then I keeping pumping money into my account and yes i am talking about the blank atm cards yes they are real. Though is illegal we all know, but there are no risks of being caught, because it has been programmed in such a way that it is not traceable,it also has a technique that makes it impossible for the CCTVs to detect you.. For details on how to get yours today, email the hackers on: bensadeghipourhackerones8@gmail.com
ReplyDeletei was lost with no hope for my wife was cheating and had always got away with it because i did not know how or
ReplyDeletealways too scared to pin anything on her. with the help a friend who recommended me to who help hack her phone,
email, chat, sms and expose her for a cheater she is. I just want to say a big thank you to
HACKINTECHNOLOGY@CYBERSERVICES.COM . am sure someone out there is looking for how to solve his relationship problems, you can also contact him for all sorts of hacking job..he is fast and reliable. you could also text +1 213-295-1376(whatsapp) contact and thank me later
Providing T00LS & Tut0rials
ReplyDeleteSpam-ming
Hac-king
Car-ding
Scri-pting
Attac-king/Phishing
Kali-Linux
De-ep W-eb Course
With Complete guidence & Proper tools
Here I'm
@killhacks Telegram
7.5.2.8.2.2.0.4.0 I'C'Q
Fullz for Filling Benefits/SBA/Unemployment/Tax Returns
SSN DOB
SSN DOB DL
High Credit Fullz
CC FULLZ With CVV [vbv & non-vbv]
Minimum CS 700+
All valid & fresh Info
Invalid/wrong info will be replace
Fresh Spa-mmed
Contact
Tele'gram @leadsupplier
I'C'Q -> 7.5.2.8.2.2.0.4.0