First You Know What is Man In The Middle Attack(MITM?
MiTM attacks pose a serious threat to online security because they give the attacker the ability to capture and manipulate sensitive information in real-time.
The attack is a type of eavesdropping in which the entire conversation is controlled by the attacker.
Sometimes referred to as a session hijacking attack, MiTM has a strong chance of success when the attacker can impersonate each party to the satisfaction of the other.
A common method of executing a MiTM attack involves distributing malware that provides the attacker with access to a user’s Web browser and the data it sends and receives during transactions and conversations.
Once the attacker has control, he can redirect users to a fake site that looks like the site the user is expecting to reach.
The attacker can then create a connection to the real site and act as a proxy in order to read, insert and modify the traffic between the user and the legitimate site.
Online banking and e-commerce sites are frequently the target of MITM attacks so that the attacker can capture login credentials and other sensitive data.
Step One:
Start Kali Linux and login, preferably as the root user. When you’ve logged in, open a Terminal and enter this command: echo 1 > /proc/sys/net/ipv4/ip_forward.
This enables IP forwarding, which is mandatory in order for the victim device to maintain connection while we are ARP poisoning it.
This command will not be permanent; you’ll have to enter it every time that you restart Kali and wish to perform another MITM attack.
Step Two:
For whatever reason, ettercap doesn’t come ready to work from the factory. We need to make some small edits before it will work.
Open a Terminal and type: leafpad /etc/ettercap/etter.conf
Open a Terminal and type: leafpad /etc/ettercap/etter.conf
Step Three:
Look through the text file that just opened. On one of the first lines, under the [privs] section, look for the words highlighted below:

You need to change the “ec_uid” and “ec_gid” values to zero. They should look like this when done: 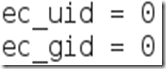
Remove the number 65534 and replacing it with 0 (zero). You can leave the “# nobody is default” line.Step Four:This next one will be tricky to locate, so we’re going to use the “Find” option. Click on Search in the toolbar at the top of leafpad and click Find, or hit Ctrl+F.Type the word iptables in the box that appears and click the Find button or press Enter.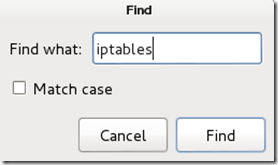
It should skip to a line that looks like this: 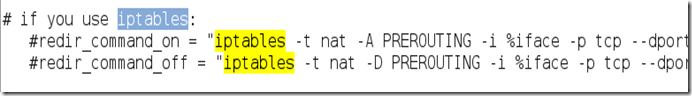
We need to “uncomment” the two bottom lines. To do this, remove the two “#” symbols before each “redir_command,” so that the two lines look like this:
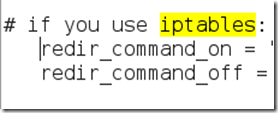
Now close leafpad and click Yes when it asks you to save changes.
Step Five:
Now start Ettercap-gtk, open a Terminal and type ettercap –G
Wait until Ettercap opens. When it does, click Sniff in the toolbar and select Unified Sniffing… from the menu.
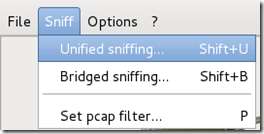
Step Six:
Select the interface that’s connected to the network.
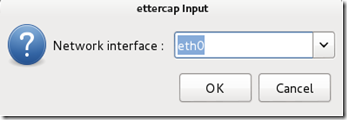
If your using a wired (ethernet) connection, then the interface will probably be eth0, but if you’re using wireless, (WLAN), then it will be a different one. To find which one of your interfaces is connected, run ifconfig.
Step Seven:
Now Ettercap should load into attack mode. Click on Hosts and select Scan for hosts from the menu.
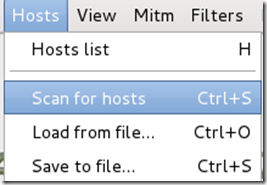
Step Eight:
Ettercap will briefly scan for hosts on the network. After a moment, you should see the words “hosts added to the host list…” in the command box.
Click on Hosts again, and this time select Hosts list from the menu.
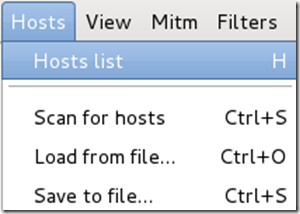
Step Nine:
Click the IP address of the router and click the Add to Target 1 button.

Then select the IP of your test victim’s machine and click Add to Target 2.

Step 10:
Now click Mitm on the toolbar and select Arp poisoning…

When the question box shows up, check the box next to Sniff remote connections and hit OK.

Step 11:
Ettercap will now Arp poison the victim and router. It might take a few minutes for the ARP process to work out, but once it does, your victim PC should be able to still connect to the internet without knowing that you’re virtually in between it and the router. If you’re victim can’t connect, make sure that you entered the “IP forward” command in Step 1 before starting ettercap.
It might be a good idea to test this attack on one of your devices first, just to make sure that everything is going as planned.
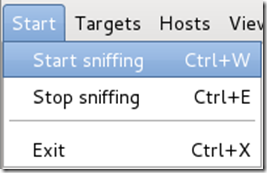
You’ve successfully executed an MITM attack!
You can now use tools such as URLsnarf and SSLstrip to sniff out information about your victim’s internet traffic. You can also use etterfilters to cut you victim’s internet completely. Tutorials on how to use these tools will be coming soon.
To stop the MITM attack, click on MITM and select Stop mitm attack(s) from the menu.
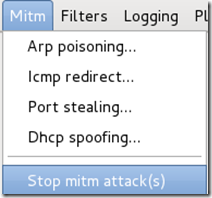
Ettercap will then send the ARP correction packet, and the network will return to normal. You can then close Ettercap.
Ways to protect yourself against one of these attacks.
There are a couple of methods:
- ARP detection software
This method is pretty useless. There are very few ARP detection programs out there, and the few that do exist are either free junk or over priced. In addition, to use these programs on a windows machine requires installing special drivers for your wireless cards. Recommendation: Don’t use.
- Static ARP entries
This method works the best for the standard individual. You just type in a simple command and your computer becomes “Unarpable.” This is how it works:
When an attacker performs an ARP MITM attack, his computer sends a ARP packet to the victim’s machine telling it that his mac address is the router’s. The victim’s machine is fooled and starts sending its data to the attacker.
When you enter a static ARP entry, you’re telling your computer that the router’s mac address is permanent and will not be changed. Therefore, your computer ignores any phony ARP packets sent by the attacker.
We will be making a tutorial on how to do this soon. In the meantime, you can use Google to find answers.
NOTE: This Is Only For Educational Purpose. I Will Not Be Responsible For Anything Done By You.



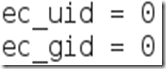











I was searching for loan to sort out my bills& debts, then i saw comments about Blank ATM Credit Card that can be hacked to withdraw money from any ATM machines around you . I doubted thus but decided to give it a try by contacting {skylinktechnes@yahoo.com} they responded with their guidelines on how the card works. I was assured that the card can withdraw $5,000 instant per day & was credited with $50,000 so i requested for one & paid the delivery fee to obtain the card, i was shock to see the UPS agent in my resident with a parcel{card} i signed and went back inside and confirmed the card work's after the agent left. This is no doubts because i have the card & has made used of the card. This hackers are USA based hackers set out to help people with financial freedom!! Contact these email if you wants to get rich with this Via email skylinktechnes@yahoo.com or whatsapp: +1(213)785-1553
ReplyDelete